As an experienced penetration tester or security professional, it is imperative that you trust the tools you work with. One way to achieve this trust is by having full transparency and familiarity with the code you are running. You are free to read, investigate, and change the build scripts for the NetHunter images. All of this goodness from the house of Offensive Security and developers of Kali Linux!
HID Keyboard and ‘BadUSB’ Attacks
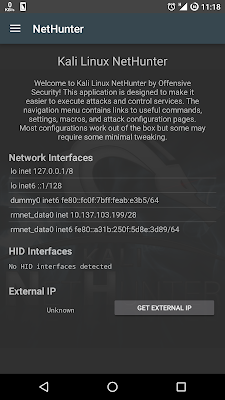
NetHunter images support programmable HID keyboard attacks, (a-la-teensy), as well as “BadUSB” network attacks, allowing an attacker to easily MITM an unsuspecting target by simply connecting their device to a computer USB port. In addition to these built in features, we’ve got a whole set of native Kali Linux tools available for use, many of which are configurable through a simple web interface.
Configuration Management
The Kali NetHunter configuration interface allows you to easily configure complex configuration files through a local web interface. This feature, together with a custom kernel that supports 802.11 wireless injection and preconfigured connect back VPN services, make the NetHunter a formidable network security tool or discrete drop box – with Kali Linux at the tip of your fingers wherever you are!
How To Install ?
1- First Of All You Need A Rooted Nexus/OnePlus One Device With TWRP Recovery,
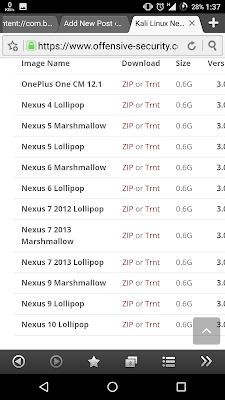
2- Download Kali-NetHunter For Your Device,
Image Name
|
Download
|
Size
|
Version
|
|
OnePlus One CM 12.1
|
|
0.6G
|
3.0
|
|
Nexus 4 Lollipop
|
|
0.6G
|
3.0
|
|
Nexus 5 Marshmallow
|
|
0.6G
|
3.0
|
|
Nexus 5 Lollipop
|
|
0.6G
|
3.0
|
|
Nexus 6 Marshmallow
|
|
0.6G
|
3.0
|
|
Nexus 6 Lollipop
|
|
0.6G
|
3.0
|
|
Nexus 7 2012 Lollipop
|
|
0.6G
|
3.0
|
|
Nexus 7 2013 Marshmallow
|
|
0.6G
|
3.0
|
|
Nexus 7 2013 Lollipop
|
|
0.6G
|
3.0
|
|
Nexus 9 Marshmallow
|
|
0.6G
|
3.0
|
|
Nexus 9 Lollipop
|
|
0.6G
|
3.0
|
|
Nexus 10 Lollipop
|
|
0.6G
|
3.0
|
|
3- Move the zip file to your root folder on your android device,
4- Reboot in Recovery,
5- Select the zip folder and flash your system,
6- Let this run for about 15-30 min..
If successful, you have successfully installed Kali Linux with Net Hunter install..
Note: Offensive Security does not provide technical support for NetHunter. Support for NetHunter can be obtained via various methods listed on the Kali Linux Community page. Further documentation can be found at NetHunter Github Wiki.
Wait  .... No Nexus ??? No OnePlus One ??? Using Any Other Android Device ???
.... No Nexus ??? No OnePlus One ??? Using Any Other Android Device ???
Here's How To Install Kali NetHunter On Any Android Device :
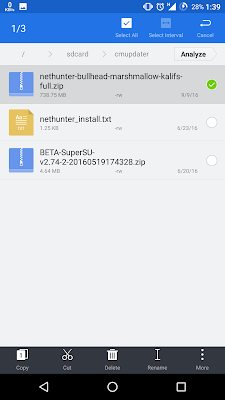
2. After you download it. you will get the file [nethunter-bullhead-marshmallow-kalifs-full.zip],
3. Extract it,
4. From the extracted folder, search for [kalifs-full.tar.xz] file, and move it to /sdcard
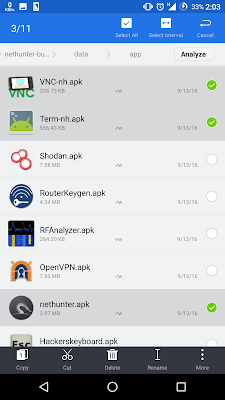
5. From the extracted folder install [nethunter.apk Term-nh.apk VNC-nh.apk] from data/app.
7. Open nethunter app and allow the permissions.
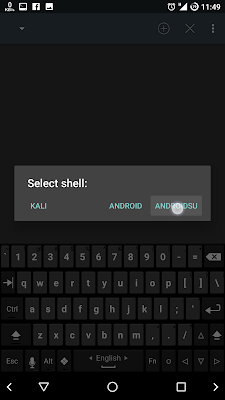
8. Open NetHunter-Terminal and choose ANDROIDSU then type the following commands :
mount -o remount,rw /system
ln -s /data/data/com.offsec.nethunter/files/scripts/bootkali system/bin/bootkali
ln -s /data/data/com.offsec.nethunter/files/scripts/bootkali_login system/bin/bootkali_login
ln -s /data/data/com.offsec.nethunter/files/scripts/bootkali_bash system/bin/bootkali_bash
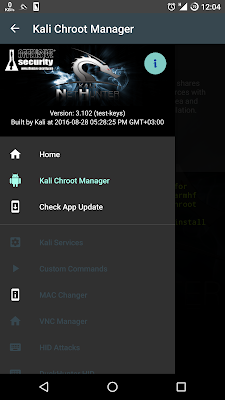
9. Open nethunter and press on Kali Chroot Manager.
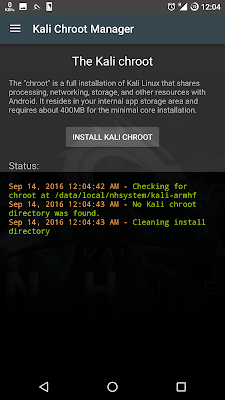
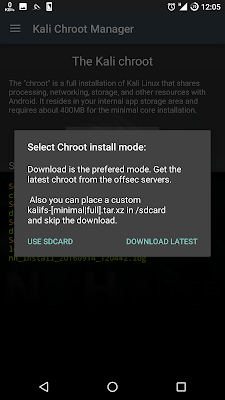
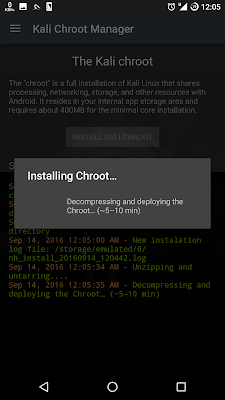
10. Choose INSTALL KALI CHROOT
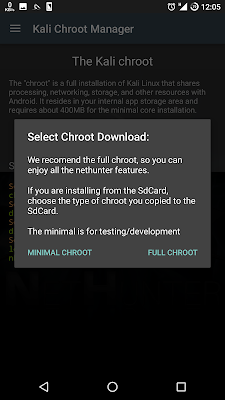
11. Choose USE SDCARD
12. Choose FULL CHROOT
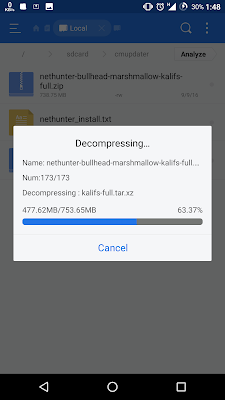
13. Installing Chroot may be take 10 minute to be completed.
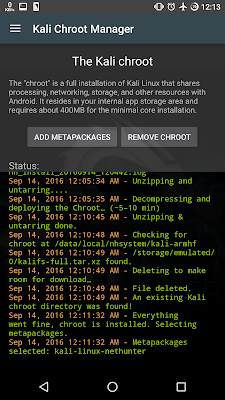
14. After complete, the file [kalifs-full.tar.xz] will be deleted.
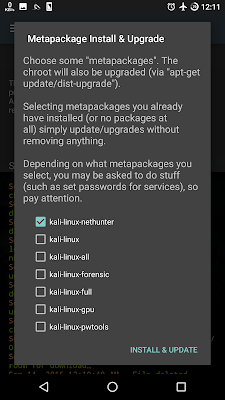
15. You can select any metapackages you want to install or ignore it.
Done !!! :)
Enjoy & Remember BE ETHICAL.
Looking for the Virtual Images of Kali Linux Penetration Testing Distribution?
and if you like this post please like & share with your friends...
& Don't Forget To....
Keep Visiting... Enjoy !!! :)