Setup Kali Linux on Raspberry Pi 3 without Display : Portable Hacking Machine
The Raspberry Pi provides a SD card slot for mass storage and will attempt to boot off that device when the board is powered on.
So Let's Get Started..
Things You Need :
- Raspberry Pi 3 : Amazon
- SD Card (16 GB) : Amazon
- Card Reader/SD Card Adoptor : Amazon
- PowerBank/Charger : Amazon
- PC/Laptop : Amazon
- Linux Operating System with Root Access : Kali Linux or ParrotSecOS
- Brain and Patience.
Installing Kali Linux on SD-Card :
2. Download Etcher for You Operating System
3. Get a fast SD card with at least 16 GB capacity and Connect it with your PC/Laptop using card reader.
4. Run Etcher, choose Downloaded .img file of Kali Linux then choose SD-Card as disk then click on Flash button.
WARNING : This Process will overwrite any existing data on your SD card. If you specify the wrong device path, you could wipe out your computer’s hard disk !!!
5. This process can take a while depending on your SD card’s device speed and image size..
Configuring Kali Linux without Display :
2. Open Terminal and move to Desktop by typing : cd /root/Desktop
3. Now Download Pi4Kali by typing : git clone https://github.com/thehackingsage/pi4kali.git
4. Connect SD-Card with your PC/Laptop using card reader, don't mount the drive.
5. Open GParted Application by typing : gparted
6. Select SD Card from the Top Right Corner.
7. Select the ext4 partition.
8. Resize the partition by dragging the right edge of the partition all the way to the right (click/drag the right edge).
9. When you are satisfied with the changes, click on the green check mark, "Return" arrow, or other "apply" control to execute these changes.
10. Mount the SD-Card.
11. Open Boot Partition of SD Card.
12. Create a simple empty file named ssh on Boot Partition of SD Card.
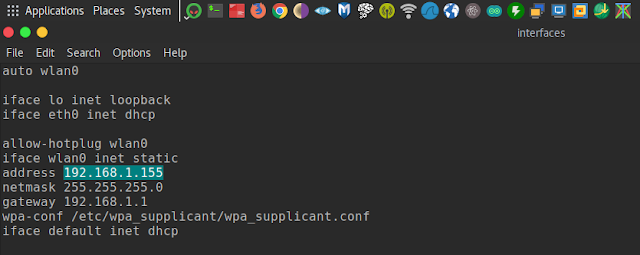
13. After that Goto Pi4kali > Config Files > etc > wpa_supplicant and open wpa_supplicant.conf in a text editor
14. Type Your WiFi SSID in the place of Type_SSID and WiFi Password in the place of Type_Password. and then save the file (ctrl+s).
15. Now go back to Config File folder and Copy the etc folder and Paste it into Root Partition of SD Card.. it will ask you for Marge and Replace Files or Folder, click on Yes..
16. Copy and Paste Pi4Kali folder in Root Partition of SD Card (/root/Downloads/)
17. Insert the SD card into the Raspberry Pi and power it on. it'll automatically login as root and connect to your wifi.
18. Now Download Putty and VNC Viewer and Install Them.
19. The Default Static IP of Your KaliPi is 192.168.1.155.
20. Open Putty And Type 192.168.1.155 in Host and 22 in Port and click on Open.
21. It'll ask you for log as : root and Password : toor
22. Now goto pi4kali folder by typing : cd Downloads/pi4kali/
23. Give execution permission to install.sh file by typing : chmod +x install.sh
24. now execute the file by typing : ./install.sh
25. Press Enter and Wait for Finish the Installation..
# It'll Update Your Kali Linux, Start Up The XFCE Desktop Environment, Configure Auto Root Login and Configure VNC Autorun on Startup..
# In The Middle of Installation It'll Ask You for VNC Password, you can type whatever password you want, then it'll ask for Enter A View-Only Password?(y/n) : Type n and Hit Enter..
26. Once the Installation process complete. restart the raspberry pi by typing : reboot
All Done.. !!!
Power On The Portable Hacking Machine :
2. Open VNC Viewer
3. Create a New Connection (CTRL+N)
4. Type 192.168.1.155:5900 in VNC Server and KaliPi in Name and click on OK.
5. Now Double Click on Kali Pi, It'll Ask You For Password So Type Your VNC Password, Check Remember Password and Click OK.
XFCE GUI Environment is Ready To Use :
# By default, the Kali Linux Raspberry Pi image has been streamlined with the minimum tools, similar to all the other ARM images. If you wish to upgrade the installation to a standard desktop installation, you can include the extra tools by installing the kali-linux-full metapackage..
6. So Open Your Terminal and Type apt-get install kali-linux-full -y and hit Enter.
That's It.. !!!
if you face any question or any problem in this process feel free to ask.. :)
and if you like this post please like & share with your friends..
Download H4CK3R The Book (An Ethical Hacking ebook For Beginners) :
https://www.h4ck3rthebook.blogspot.com
Twitter : https://www.twitter.com/thehackingsage
Instagram : https://www.instagram.com/thehackingsage
Github : https://www.github.com/thehackingsage
& DON'T FORGET TO SUBSCRIBE..!!!
YouTube : https://www.youtube.com/hacktronian
Happy Hacking !!!
Labels: Raspberry Pi