BurpSuite Pro, Plugins and Payloads
Burp Suite is a reliable and practical platform that provides you with a simple means of performing security testing of web applications. It gives you full control, letting you combine advanced manual techniques with various tools that seamlessly work together to support the entire testing process. The utility is easy-to-use and intuitive and does not require you to perform advanced actions in order to analyze, scan and exploit web apps. It is highly configurable and comes with useful features to assist experienced testers with their work.
The main window displays all the available tools you can choose from and set each one's settings the way you want.
Being designed to work alongside your browser, the application functions as an HTTP proxy, thus all the HTTP/s traffic from your browser passes through the utility. This way, if you want to perform any kind of testing, you need to configure the browser to work with it.
The first thing you need to do is to confirm that the app's proxy listener is active. Simply navigate to the Proxy tab and take a look in the Proxy Listeners section. You should see an entry in the table with the Running check box ticked. The second thing you are required to do is to configure your browser to use the app's proxy listener as its HTTP proxy server. Finally, you need to configure the browser to be able to send HTTP requests through the app without problems.
The previously mentioned utility gives you complete control over all of the actions you want to perform and get detailed information and analysis about the web applications you are testing. Using tools such as Intruder, Repeater, Sequencer and Comparer you are able to carry out different actions with ease.
With the help of Spider, you can crawl an application to locate its content and functionality. You are able to add new scope by selecting the protocol and specifying the host name or the IP range. Then the utility monitors all the transferred bytes and queued requests.
The Intruder tool enables you to perform attacks against web apps. Simply set the host name and the port number, define one or more payload sets and you are done. You can also use the HTTP protocol by checking the proper box from the Target tab.
Another tool that automates testing tasks is called Sequencer, which analyzes the quality of randomness in an application's session tokens. Firstly, you need to load at least 100 tokens, then capture all the requests.
Overall, Burp Suite Free Edition lets you achieve everything you need, in a smart way. It helps you record, analyze or replay your web requests while you are browsing a web application.
- Burp Proxy
- Burp Spider
- Burp Repeater
- Burp Sequencer
- Burp Decoder
- Burp Comparer
- Burp Intruder
- Burp Scanner
- Save and Restore
- Search
- Target Analyzer
- Content Discovery
- Task Scheduler
- Release Schedule
https://github.com/thehackingsage/burpsuite
More Payloads : https://github.com/swisskyrepo/PayloadsAllTheThings
Requirements :
Burp requires a computer with the official Java Runtime Environment (64-bit edition, version 1.6 or later) installed.
Download the latest Java Runtime Environment (JRE) : Click Here
How To Use Burp Suite Pro ? :
- Download BurpSuitePro as ZIP : http://bit.ly/burpsuitepro
- extract and open folder
- open BurpSuite-Keygen.jar with java
- open BurpSuite-Pro-v1.7.37.jar with java
- copy-paste Licence from Keygen to BurpSuite and Click on Next
- choose Manual Installation and copy-paste Activation Request from BurpSuite to Keygen
- now copy-paste Activation Response from Keygen to BurpSuite
- click next and your pro version will activate
Note : you don't have to repeat this process again and again to use it. after doing it once Windows User run .bat file & Linux User run .sh file to use the BurpSuitePro..
if you face any problem feel free to ask..
How To Use Burp Suite Plugins ? :
- open BurpSuite
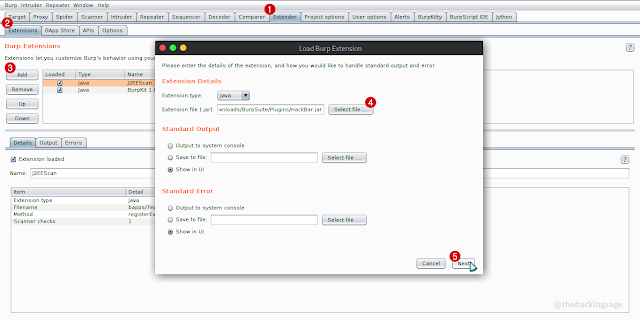
- go to Extender > Extensions
- click on Add and Select .jar file & then click on Next
That's It !!!
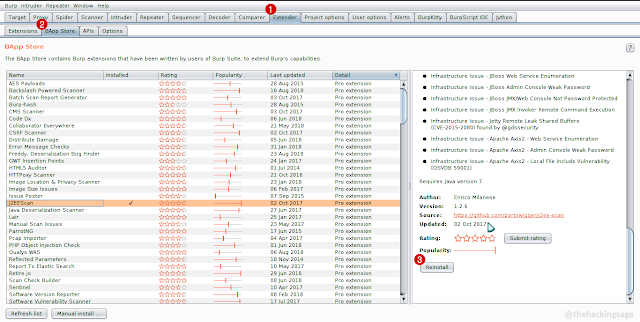
Note : One More Thing You Need To Know That Now You Are Using BurpSuite Pro So Now You Can Also Use All Pro Extensions From BApp Store.
Video Tutorial :
YouTube : Soon
That's It !!!
if you like this post please like & share with your friends..
Download H4CK3R The Book (An Ethical Hacking ebook For Beginners) :
https://www.h4ck3rthebook.blogspot.com
Twitter : https://www.twitter.com/thehackingsage
Instagram : https://www.instagram.com/thehackingsage
Github : https://www.github.com/thehackingsage
& DON'T FORGET TO SUBSCRIBE..!!!
YouTube : https://youtube.com/hacktronian/
Happy Hacking !!!
Labels: Bug Bounty, BurpSuite, Downloads, Linux, Penetration Testing, Plugins, Vulnerability, Web Application, Website Hacking, Windows 10